Disclaimer - Curated Intelligence is a private trust group and members are able to publish their research under our banner without it being attributed to them. We thank our members for their contribution.
Members of Curated Intelligence have recently tracked a new
global credential harvesting campaign targeting Microsoft accounts. This latest
wave of phishing attacks masquerade as ‘shared document’ notification emails which
deliver an embedded URL. If clicked, it leads to a fake Adobe Document Cloud
application login page to harvest credentials for Outlook and Office 365.
Many countries were targeted in this campaign; however, the
US and the UK have seen most of the targeting, followed by the Netherlands.
Other targets possibly include Germany, France, Sweden, Portugal, Spain, Italy,
India, Australia, Belgium, Slovenia, Poland, Chile, Norway, Romania, Canada,
Turkey, Singapore, Japan, and Hong Kong.
The campaign is believed to have been delivered via a range
of phishing emails that have varied in content depending on the target. Some
emails requested that the user visit a landing page to view an “encrypted”, “scanned”,
or “faxed” document (see Fig. 1). These initial links commonly used the Cloudflare
content delivery network (CDN) workers[.]dev to evade anti-phishing detection systems.
Fig. 1 – Example
of a Phishing email template sent in this campaign
Throughout this campaign, Curated Intel analysts identified
that part of the infrastructure was deliberately tailored to its targets. This
shows the threat actors had likely researched their targets before conducting
launching phishing emails against specific targets from a predetermined list.
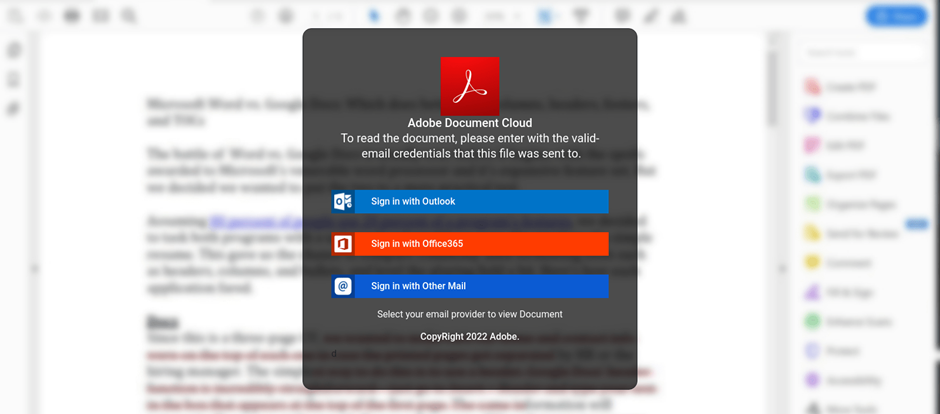
The embedded URL in the phishing emails redirect users to a
convincing web application, often delivered via another third-party CDN. The
application was designed to trick the user into thinking they were logging in
to the Adobe Document Cloud application. However, it collects and exfiltrates
any login credentials entered by the user before redirecting them to the
genuine ‘login.microsoftonline.com’ URL.
Fig. 2 –
Credential stealing Adobe Document Cloud-themed landing page
What was notable about this campaign to Curated Intelligence
analysts was that it had largely reused the same infrastructure for redirection
links and to host landing pages. This includes “share[.]sender[.]net”, “worker[.]dev”,
and “erpnext[.]com” hostnames. Over the course of a six-month period, Curated
Intelligence analysts observed up to 134 unique URLs. There are almost
certainly many more URLs related to this campaign, that were not identified by
Curated Intelligence.
There was one common artefact about this campaign that
enabled Curated Intelligence analysts to track this wave of attacks: the Firebase
site “runn1rnl8xzmqeh0kvov[.]web[.]app” that was used for data exfiltration.
This Google Firebase site was present in all the fake Adobe Document Cloud landing
pages. Curated Intelligence reported the main Google Firebase site, along with
our research, to the UK’s National Cyber Security Centre (NCSC) for enforcement
action.
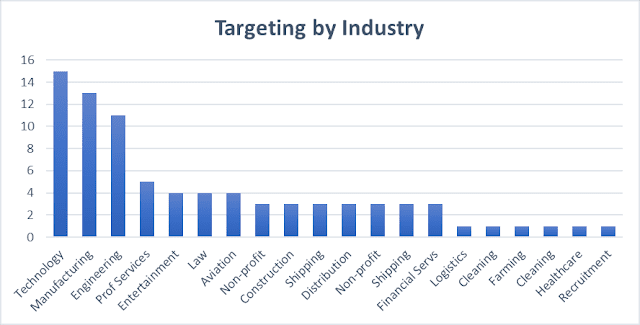
This campaign was traced back to at least August 2021 and
has targeted organisations from a variety of industry verticals. The graphs
below (see Fig. 3 and Fig. 4) show distribution of phishing targets based on
industry vertical and by country the organisation is based.
Fig. 3 – Phishing
targets per industry vertical
Fig. 4 – Phishing
targets per country
The threat actor behind the attacks must have had access to
considerable resources due to the sheer breadth of the infrastructure used and
the effort taken to stand it up. It is believed that the threat actor behind
the campaign is a cybercriminal group aimed at business email compromise (BEC)
for financial gain. The size of the infrastructure used in this campaign,
however, does show considerable effort and resource.
Curated Intelligence analysts also identified that many of
the organisations targeted in this campaign were small to medium upstream
suppliers to critical national infrastructure. If compromised successfully,
these could potentially be used by these threat actors as a foothold from which
more significant organizations may be targeted.
Indicators
of Compromise (IOCs)
Data Exfiltration site:
- runn1rnl8xzmqeh0kvov[.]web[.]app
Abused Legitimate Services:
- share[.]sender[.]net
- workers[.]dev
- erpnext[.]com
- onedrive[.]live[.]com
- 1drv[.]ms